Generate millions of passwords
This product lets you generate millions of passwords and usernames in a matter of minutes. The precise speed and the number of passwords that can be generated depend on the available memory and processor speed. We guarantee ability to generate at least 50 000 000 passwords, provided there is enough memory (each password requires 2 × n + 4 bytes of storage, where n is the number of characters in a password, and 2 bytes per character are due to passwords being in Unicode).
Generate Directly to File PRO
The product can generate passwords, directly writing them to a file on disk, completely bypassing User Interface. This will not only result in considerable speed up and save system resources, but will allow you to generate truly large number of passwords, in excess of tens of millions!
5 Generation Modes
The product offers 5 different generation modes, each with different options and functionality. The kind ofrandom numbers / keycodes you want to generate will influence the generation mode you select.
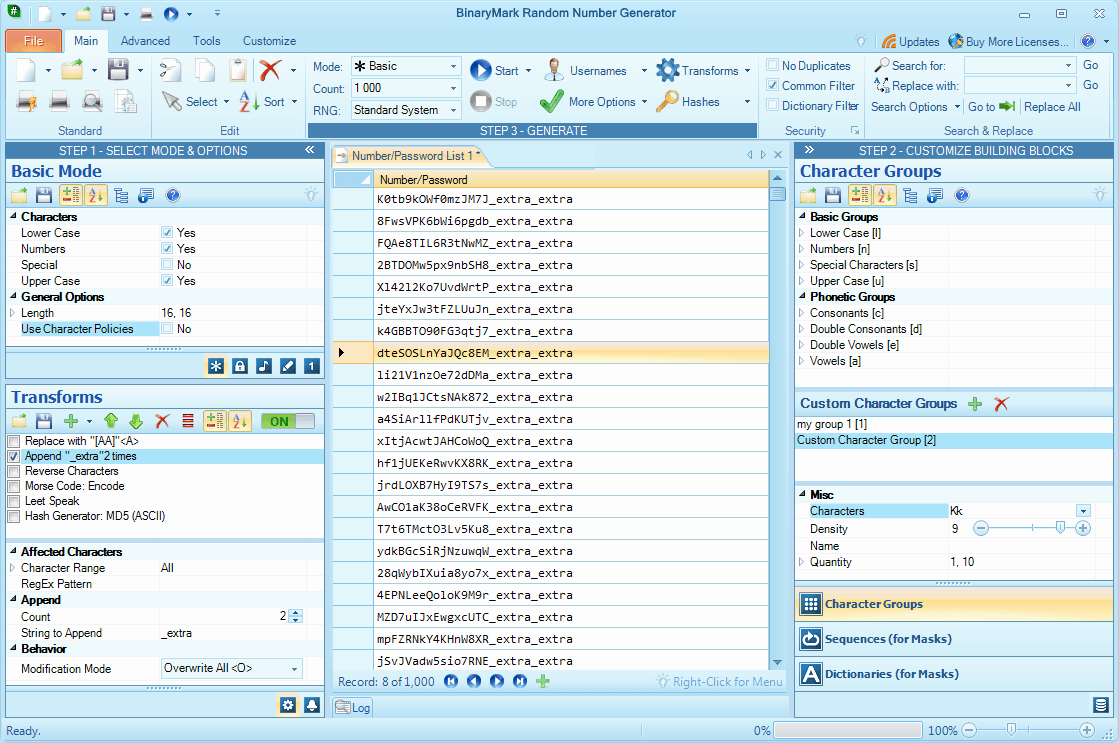
Basic Mode
If all you want is just quickly generate strong passwords, without having to go through many options, Basic Generation Mode is there for you. It lets you specify the length, turn on or off lower case characters, upper case character, numerals, special characters, as well as enable or disable character policies (see below).
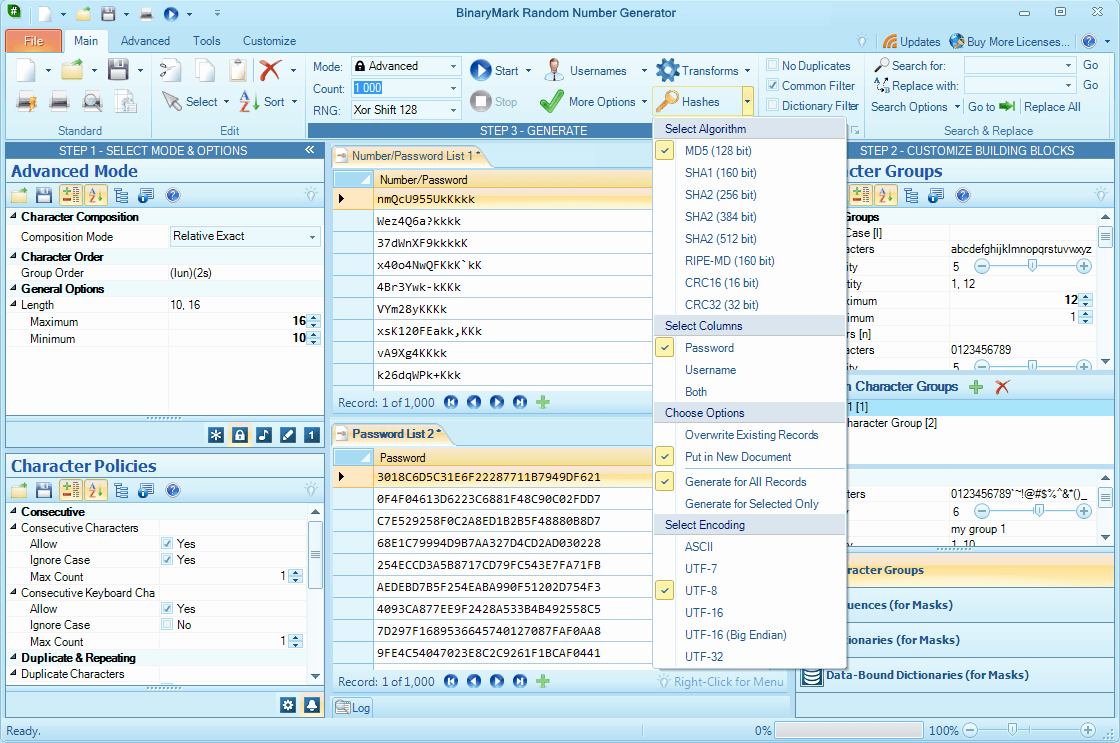
Advanced Mode
Advanced mode is similar to Basic Mode, except it has far more options. It allows you to control precisely what characters you want to see in your passwords and what characters you do not want to see appearing. In addition, you can control how often a particular character or group of characters will appear, as well as where (roughly) it will be placed – at the beginning, in the middle, at the end, or somewhere randomly.
Sample case would be: password that contains lower case, upper case, and numeric characters with 10:10:5 ratio, excluding Capital letter B, and it should not start with a number.
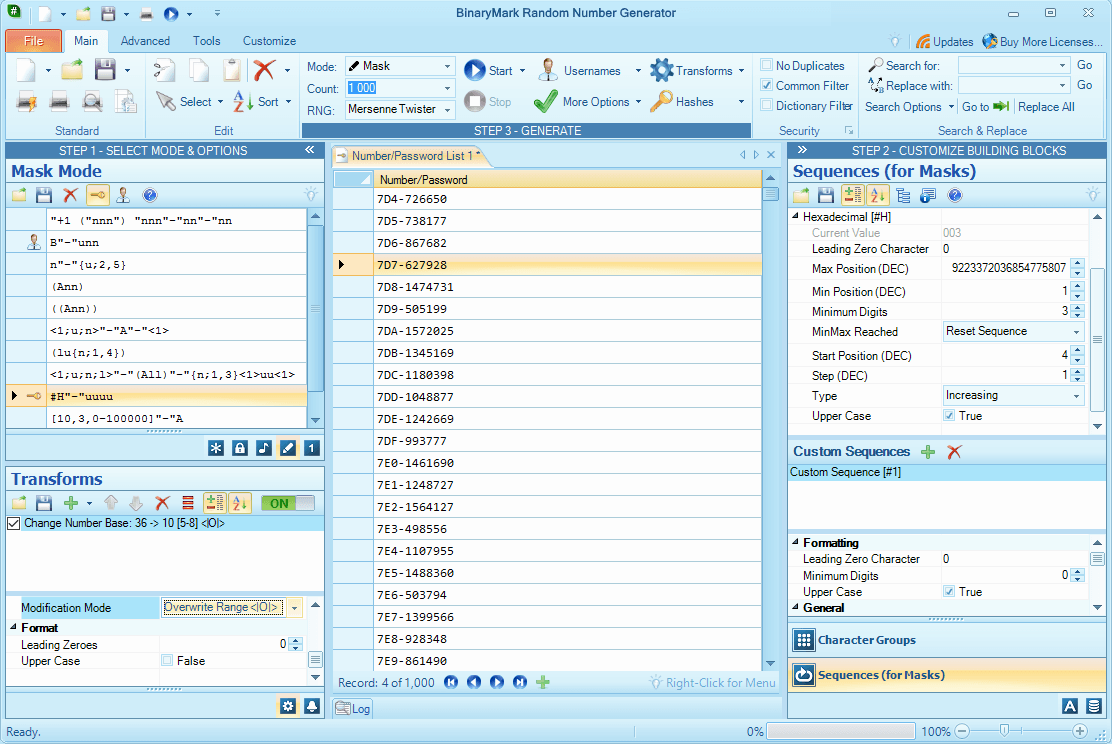
Mask Mode PRO
Masking Mode is different from the previous two modes in a number of ways. First and foremost, it gives you complete control over character placement. It can still be random, of course, but you can precisely control the boundaries of this randomness.
In addition, it allows you to use more sophisticated 'building blocks' in your passwords: words or items from external files / databases, and sequential numbers – parts that are automatically incremented with every new password generated.
On top of that, masking mode has several 'operators' that give you even more flexibility. For example, random distribution operator (...) can be used if you want to randomly distribute building blocks (be it characters, words, or sequences) in certain part of the mask.
Pronounceable Mode
Pronounceable Mode makes it super easy to generate passwords that are easy to pronounce. It too has several unique options. For instance, you can enable usage of double vowels and consonants, so that passwords like 'umbrella' would be possible.
Number Mode PRO
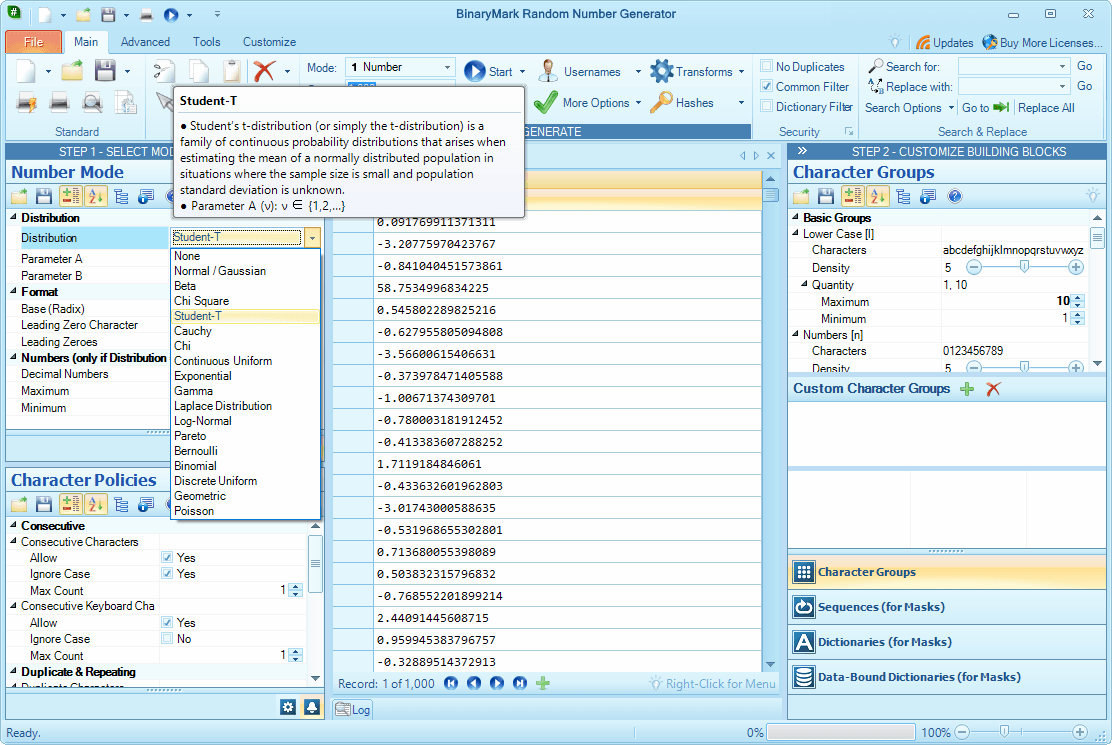
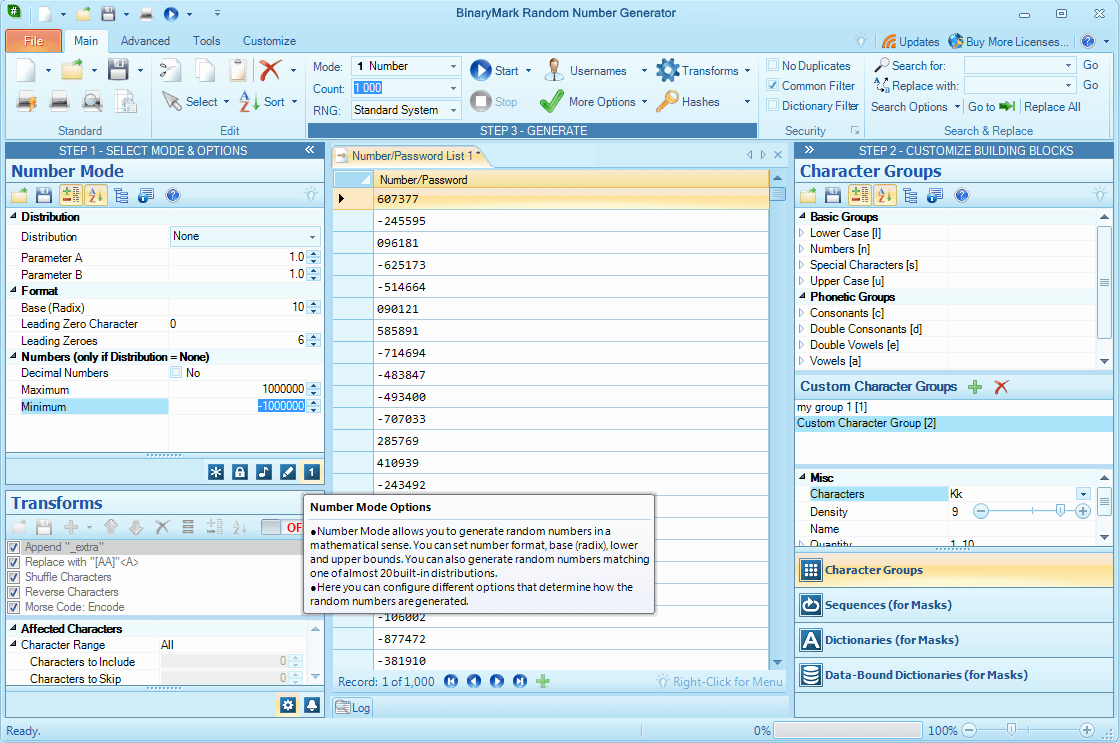
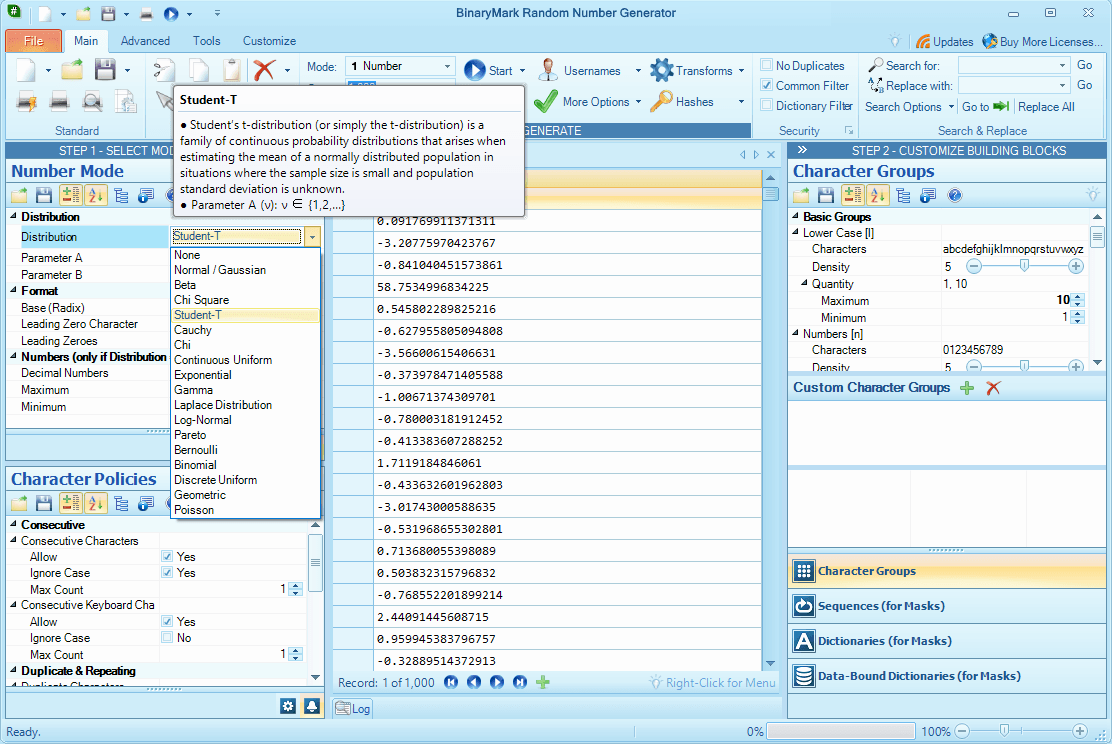
Number Generation Mode allows you to generate random numbers (whole, negative, floating point) in mathematical sense of a word. You can specify number range within which the generated numbers should fall. You can also have the generated numbers match a given statistical distribution like Normal, Geometric, or Uniform (there are 17 built-in distributions - both discrete and continuous).
Generate Random Numbers
You can generate random numbers within a specified range or matching a given distribution.
17 Built-in Statistical Distributions
You can generate random numbers that will form a given statistical distribution.
The following continuous distributions are supported: Normal / Gaussian, Beta, Chi Square, Student-T, Cauchy, Chi, Continuous Uniform, Exponential, Gamma, Laplace, Log-Normal, Pareto
The following discrete distributions are supported: Bernoulli, Binomial, Discrete Uniform, Geometric, Poisson
Random Numbers within range
Generate whole or fractional random numbers within specified range. You can set the lower bound to be less than zero to generate negative numbers.
Use different numeric bases (radix)
You can specify the format of the generated random numbers, including its base (radix). You can specify any base between 2 and 36, including binary, octal, decimal, and hexadecimal.
Other formatting options include leading zero character selection, minimum length in digits.
Character Groups
Character Groups are distinct collections of characters grouped together for convenience. They make it easy to control password composition and character placement. For example, if you place a lower case character group placeholder in a mask, you can precisely control where lower case character(s) should appear. What's more is that you can easily remove and add characters from a character group. That way you can exclude unwanted characters with a single click!
There are 4 built-in basic character groups, 4 built-in phonetic character groups, and you can define up to 9 custom character groups - each with arbitrary set of characters, including non-ASCII characters!
Basic Character Groups
There are 4 Basic Character Groups: lower case, upper case, numeric, and special (punctuation and others).
Phonetic Character Groups
There are 4 Phonetic Character Groups: vowels, consonants, double vowels, and double consonants. These character groups are mainly used by the Pronounceable Generation Mode, but you are free to use them in Advanced and Masking Mode as well, though the last two phonetic character groups would be hardly useful in modes other than Pronounceable.
User-Defined Character Groups
You can create up to 9 custom character groups. Each custom character group can contain an arbitrary set of characters, including non-ASCII, Unicode characters. Custom character groups allow you to create groups of characters that make sense to you and help you accomplish your goals.
Advanced Masks PRO
Masks can be thought of as blueprints for the passwords / codes you want to generate. While the masks are used by only 2 generation modes – Advanced and Masking, they are extremely useful.
In Advanced Generation Mode only simple masks are allowed, though you still can accomplish quite a lot with them. For example, (lun)sn is a perfectly valid mask for Advanced Mode. In this case it means that the first part of a password will consist of upper case, lower case, and numeric characters intermixed with each other, followed by special (punctuation and miscellaneous) characters, followed by numeric characters. In the Advanced Mode, the precise number of characters for each character type is determined by the appropriate character's group Density property and the passwords overall length.
In Masking Mode, the masks can be much more sophisticated, as they can contain operators, sequences, words, literals, and even data taken from outside sources. A thing to note is that in the Masking Mode, in contrast with Advanced Mode, a character group placeholder always corresponds to a single character from that group (whereas in Advanced Mode character group placeholder may correspond to more than one character from that group - see above).
Mask / Pattern Resources
Masks, and ultimately the passwords which they correspond to, can be though to consist of distinct building blocks, or resources, and operators that manipulate these resources. There are several kinds of resources that masks can contain:
- Character Group Placeholders - these will be replaced with actual characters from the appropriate character groups.
- Dictionary Placeholders - these will be replaced with words or items taken from built in dictionaries, external text files, or even databases.
- Sequence Placeholders - these represent parts of the password that are supposed to be incremented by a fixed amount with every new password being generated. Sequences can be binary, decimal, hexadecimal, alphanumeric, or of arbitrary base. See sequences feature for more information.
- Literals - these represent unchangeable pieces of text that you type-in.
This wide variety of building bocks gives you an idea of how flexible the program is.
Mask / Pattern Operators
In addition to resources, masks can have operators that manipulate those resources. Here are some of the masking operators:
- Random Element Distribution
(…) - randomizes the relative placement of all resources within the parentheses, such as individual characters, words, sequences, and literals.
- Random Character Distribution
((…)) - randomizes the relative placement of all characters within the parentheses, even if it contains composite resources like words, sequences, and literals (thus it destroys words, random numbers, sequences, as the position of all constituent characters is randomized).
- Random Length
{<Char-Group-Placeholder>; <min>, <max>} - takes random characters from the appropriate character group between <min> and <max> number of times.
- Range
[<BaseN>, <Number-Of-Digits>, <min>, <max>] - returns a formatted random number of base <BaseN> with a value between <min> and <max>.
- Random Placement - a complex operator that allows for scenarios such as if Part A is here, then Part B is there, and PART C is over there, and vice versa (parts here represent submasks, and their number is arbitrary).
But that’s not all – operators can be nested in one another, which gives you truly infinite possibilities.
Use Words & Text Items PRO
You can use words or other textual items in your passwords! These items can be taken from any of the 4 built-in Dictionaries, your own Dictionary (practically an external text file), or even from a Database.
In addition you can control which items are to be taken with various filters, and how they are supposed to be manipulated using letter-case masks, and other tools. And what's more - you can have several such textual items in your password!
- From built-in "dictionaries" -There are 4 built-in dictionaries (collections of 'words') in the program: Default (nouns, adjectives, verbs), Given Names, Family Names, and Movie Characters - overall totaling at around 90 000 words.
- From user-defined text files - You can also use words taken from external textual files in your passwords. These external textual files are regarded as user-defined dictionaries by the program, where each line is treated as a word. All the settings that you can apply to built-in dictionaries are applicable for user-defined dictionaries as well. For instance, before a word is inserted, it can be capitalized, first few letters removed, tuned into uppercase, etc.
- From databases - You can use data from any ODBC-compliant database where source of data is a database, and words are items returned by the SELECT SQL query.
Use Sequences like 009, 00A, 00B... PRO
Sequences are quite far from being random. Essentially they are elements that you can use in masks, whenever you want the codes you are generating to have incrementally adjusted and formatted parts. For example, you may want to generate 10 000 codes, where first 5 characters should be in the form 00001 through 10000, i.e. this part should be incremented by 1 starting from 00001 and formatted with all leading zeros included. Sequences allow for exactly such a thing!
But sequences need not be decimal. They can be binary, hexadecimal, alphanumeric, or in fact of any base up to base 36. In addition, you can specify starting value, increment amount (positive to advance, negative to decrement), maximum and minimum value, and other settings. You can define up to 9 custom sequences.
Also note that sequences are a nice way to make sure that all generated passwords / codes are unique (but there is a special uniqueness setting as well).
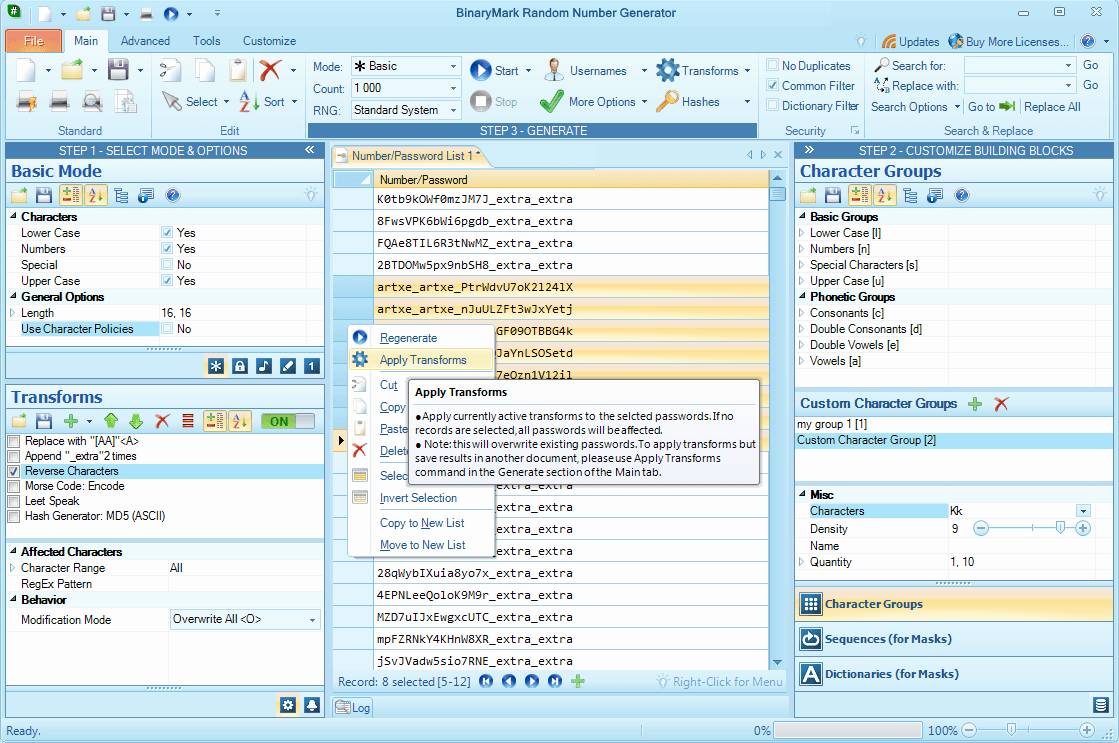
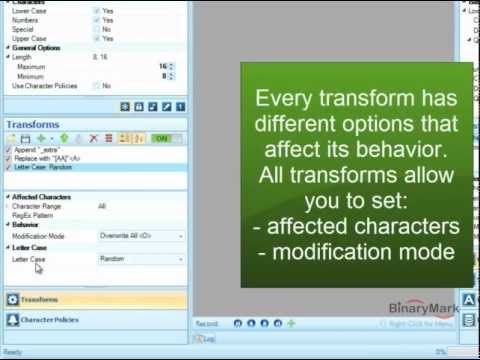
Text Transformations PRO
Various built-in transforms can be applied to generated passwords as the last step in the generation process or even to the already generated passwords. Transforms allow you to further fine-tune the passwords being generated, enabling you to add, replace, or remove strings of text; affect the casing or order of characters; convert generated strings to Morse code, Leet Speak, Base-64; generate hashes, and get character codes; and perform other manipulations.
You can apply multiple transforms in a sequential manner. You can also specify exactly which characters in the original string should be affected (you can set the starting and ending characters and / or set RegEx pattern that should match only specific characters). You can specify how the transformed string should be merged with the original: you can set it to overwrite original, overwrite affected characters only, insert before or after the original.
Replace, Insert, Delete Text
There are different transforms that allow you to replace specific characters and text strings in the generated passwords. You can also insert or append new string literals; or even remove certain unwanted strings.
Morse Code Conversion
You can convert applicable characters in the generated strings to their Morse Code equivalents.
Leet Speak Conversion
You can convert applicable characters in the generated strings to their Leet Speak equivalents.
Base-64 Conversion
You can encode generated passwords in base 64.
Characters: Reverse, Shuffle, Change Case...
You can perform various manipulations on individual characters like changing letter case. In addition you can reverse, shift by a certain amount, or randomize the order of characters.
Convert Number Base
Provided that the generated string is a number, you can convert its base (radix) to any other base between 2 and 36.
Compute hashes
You can compute hashes of generated strings in the specified encoding and using specified hashing algorithm: SHA1, SHA2, MD5, RIPE-MD, CRC.
Many Other Transforms
There are many other transformations that you can perform, including getting Unicode character codes, byte codes, performing HTML & URL encode / decode operations.
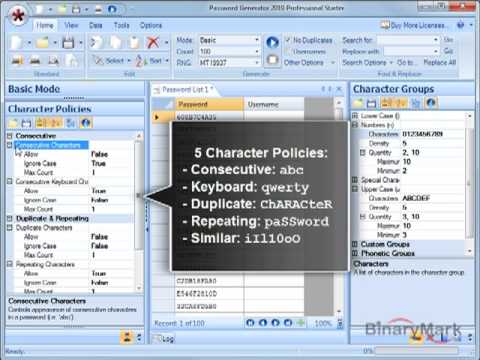
Character Policies PRO
Character Policies are special options that you can turn on and off (and tweak a little) that make sure certain conditions and requirements are met for the passwords being generated. For example, your policy may be that you allow no more than 2 consecutive characters in your passwords, so that abedgh is allowed, but not abcefg; or maybe you are not allowing repeating characters like the letter s in the word password. In all these cases, character policies help you ensure that all these restrictions are followed.
Consecutive Characters
A Consecutive Character policy, when activated, makes sure that no more than the specified number of consecutive characters appears (1 by default, which means no consecutive characters are allowed).
Consecutive characters are those that appear next to each other and form a sequence. In that regard, there are 2 versions of this policy: one for logical consecutive characters like abc, or 123, and one for keyboard consecutive characters like qwerty.
So for example, the word about will not be allowed, as the letters a and b form a forbidden sequence.
You can also specify whether or not to treat lower case and upper case variants of the same letter as being the same.
Similar Characters
A Similar Character policy, when activated, makes sure that no predefined similar characters can appear in a password at all. This is usually applied to 0 o O 1 i I l characters.
Repeating Characters
A Repeating Character policy, when activated, makes sure that no more than the specified number of repeating characters appears (1 by default, which means no repeating characters are allowed).
So for example, the word password will not be allowed, as the letter s is repeated.
You can also specify whether or not to treat lower case and upper case variants of the same letter as being the same.
Duplicate Characters
A Duplicate Character policy, when activated, makes sure that no more than the specified number of duplicate characters appears (1 by default, which means no duplicate characters are allowed).
This is actually a superset of Repeating Character Policy case; because here we do not allow characters to appear more than the specified number of times regardless of where they are in a password (they need not be next to one another, as in the Repeating Character Policy, for this policy to be triggered). So, if this policy is enabled, then the Repeating Character Policy is practically ignored.
So for example, the word password will not be allowed just as the word suspend, as the letter s appears more than once.
You can also specify whether or not to treat lower case and upper case variants of the same letter as being the same.
Pseudo-Random Number Generators
How does the program generate random passwords? That is where does the randomness come from?
At the core of the generation process is the Random Number Generator (RNG), which creates randomness that the program then uses to make random choices, such as character selection and placement.
The product comes with 5 different internal random number generators that you can choose from. In choosing an RNG there is usually an associated tradeoff between the speed and randomness (which implies security, as more random = better security): the better randomness RNG generates, the slower it is.
The fastest RNG is XOR-Shift 128, which is a xorshift pseudo-random number generator with period 2^128-1. The most secure RNG, and the one which generates the best randomness, is the FIPS-140 compliant Cryptographically Secure RNG. The other 3 RNGs are: Mersenne Twister pseudo-random number generator with period 2^19937-1; Additive Lagged Fibonacci pseudo-random number generator that uses the modulus 232, and by default the 'lags' 418 and 1279; and the one provided by the system.
You can to an extent control RNGs by setting the value for the initial random seed.
Username Generation PRO
You can generate usernames along with passwords, much the same way as you generate passwords. Usernames are generated according to a specified mask. You can then export generated usernames along with passwords to a database, or use them to update existing passwords in a database.
Unicode Support for non-ASCII characters
Your passwords can contain non-ASCII characters, as the program has full support for Unicode. In fact, as you define your own character groups, you can easily add non-ASCII characters into them. In fact, you can generate passwords and usernames with no Latin letters at all, but with say Cyrillic letters. This gives you full flexibility.
Keycode Generation
With such advanced masking capabilities, support for multiple sequences in a single mask, and ability to insert external data from databases into your keycodes, you can easily create all kinds of keycodes for all your needs: be it generating unique lottery ticket numbers, pin codes, serial numbers, or anything else!
Hash Generation - SHA, MD, CRC… SVR
The program lets you generate not just passwords, keycodes, and usernames, but also their hashes, that you can later save or export. The supported hash formats include: SHA-3, SHA-2 (512, 384, and 256 bits), SHA-1 (160 bits), MD-5 (128 bits), RIPE-MD (160 bits), CRC (16 & 32 bits).
User Notification by E-Mail SVR
One of the common tasks of IT security professional is to make sure that personal data of all employees in an organization is safe and secure. Part of this is making sure that all user passwords are strong and are changed on a regular basis.
While changing the passwords may not be so difficult, notifying users about the changes could be a bit of a hassle. This is where program's User Notification Wizard can help. It works by automatically e-mailing users their new passwords, thus saving you a lot of time!
Command-Line Random number Generator SVR
Server Edition of the product, which is available on request, comes with a command-line version of the password generator that offers virtually all features of the main application in a command line format, so that it can be easily automated and scheduled to run on a regular basis.
API - Signed .NET DLL Random number Generator Library
Developer Edition of the product, which is available on request, comes with an API for all password generation features in the form of a signed .NET 2.0+ Compatible DLL library and detailed documentation. If you need to tightly integrate our password generator with your business logic, or want to use its password generation capabilities in your applications, then Developer Edition is for you!